Take note: In exceptional situation, dependant upon cellular copyright configurations, you might require to exit the website page and check out yet again in a number of hrs.
??Moreover, Zhou shared the hackers begun making use of BTC and ETH mixers. As being the name indicates, mixers mix transactions which even more inhibits blockchain analysts??ability to monitor the cash. Following the use of mixers, these North Korean operatives are leveraging peer to look (P2P) sellers, platforms facilitating the direct acquire and advertising of copyright from 1 consumer to a different.
Discussions all over security while in the copyright industry will not be new, but this incident once again highlights the need for improve. Plenty of insecurity in copyright quantities to a lack of primary cyber hygiene, an issue endemic to corporations across sectors, industries, and international locations. This field is filled with startups that improve quickly.
Unsuccessful: Your identification verification may very well be unsuccessful as a result of many things, such as incomplete details or the necessity For added information. You may be prompted to try once again to recheck and resubmit your facts. Please chat with the agent if you need support.
three. To incorporate an additional layer of protection for your account, you will end up requested to enable SMS Authentication by inputting your cell phone number and clicking Deliver Code. Your technique of two-issue authentication can be adjusted at a afterwards date, but SMS is necessary to complete the register method.
Safety starts with being familiar with how builders accumulate and share your knowledge. Info privacy and security tactics may well fluctuate depending on your use, region, and age. The developer provided this information and facts and should update it after a while.
It boils all the way down to a supply chain compromise. To carry out these transfers securely, Just about every transaction demands a number of signatures from copyright workforce, called a multisignature or multisig course of action. To execute these transactions, copyright relies on Protected Wallet , a 3rd-bash multisig platform. Previously in February 2025, a developer for Safe and sound Wallet fell to get a social engineering attack, and his workstation was compromised by destructive actors.
Hi there! We observed your critique, and we wished to Verify how we may perhaps support you. Would you give us a lot more particulars regarding your inquiry?
copyright companions with main KYC distributors to deliver a speedy registration course of action, so that you can confirm click here your copyright account and buy Bitcoin in minutes.
Some cryptocurrencies share a blockchain, even though other cryptocurrencies operate on their own individual blockchains.
This incident is more substantial in comparison to the copyright market, and this kind of theft can be a subject of world protection.
Furthermore, it appears that the danger actors are leveraging income laundering-as-a-services, furnished by structured crime syndicates in China and countries in the course of Southeast Asia. Use of this service seeks to even further obfuscate money, cutting down traceability and seemingly using a ?�flood the zone??tactic.
Plainly, This really is an very rewarding venture to the DPRK. In 2024, a senior Biden administration official voiced worries that about fifty% from the DPRK?�s overseas-currency earnings arrived from cybercrime, which includes its copyright theft pursuits, along with a UN report also shared statements from member states that the DPRK?�s weapons software is largely funded by its cyber operations.}
 Jaleel White Then & Now!
Jaleel White Then & Now! Andrew Keegan Then & Now!
Andrew Keegan Then & Now!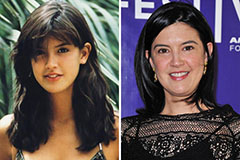 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Meadow Walker Then & Now!
Meadow Walker Then & Now! Sarah Michelle Gellar Then & Now!
Sarah Michelle Gellar Then & Now!